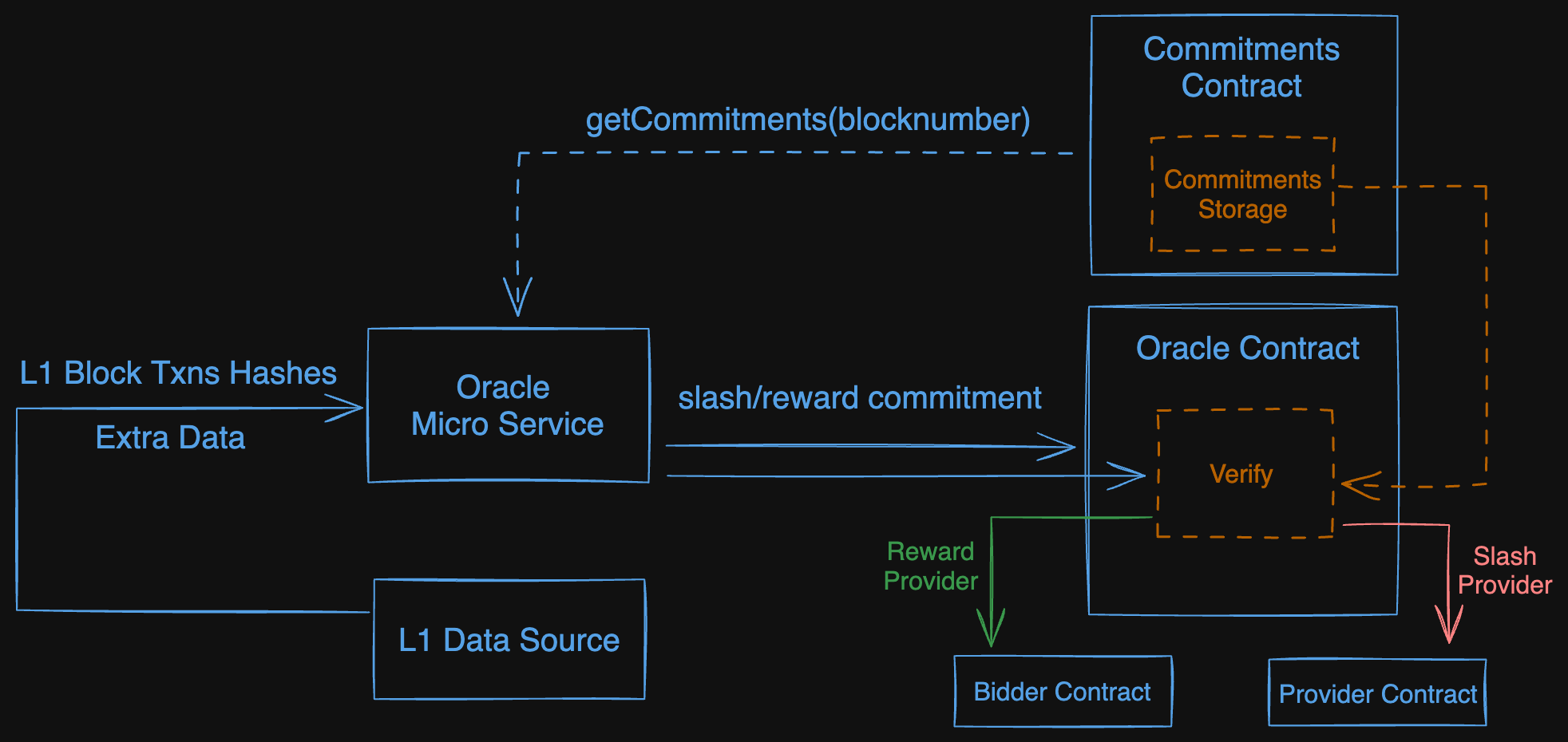
Prior to Oracle Engagement
Before the oracle can be engaged according to the protocol’s intended sequence of events, several preliminary actions must be taken: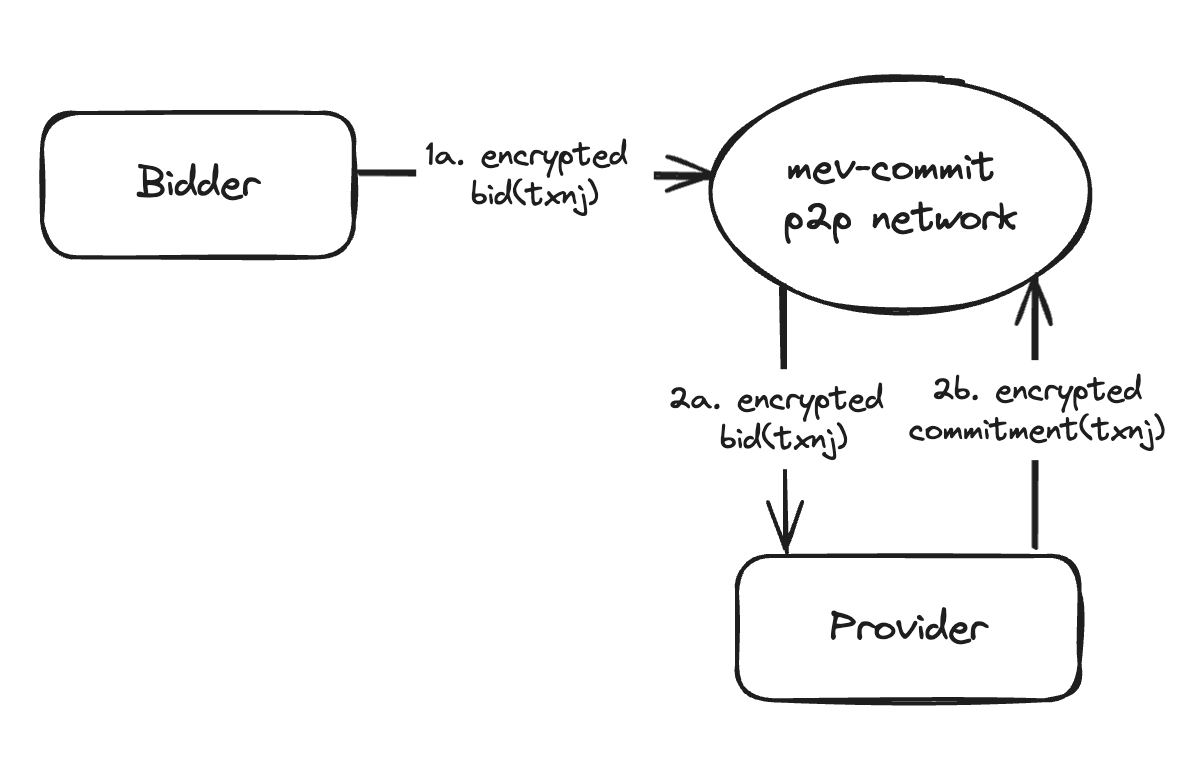
Oracle Happy Path Flow
When a bid for a transaction (txnj) is circulated through the mev-commit p2p network, and the provider has made an encrypted commitment and then opened it after the L1 block was created, the oracle is activated to verify whether the provider has honored this commitment.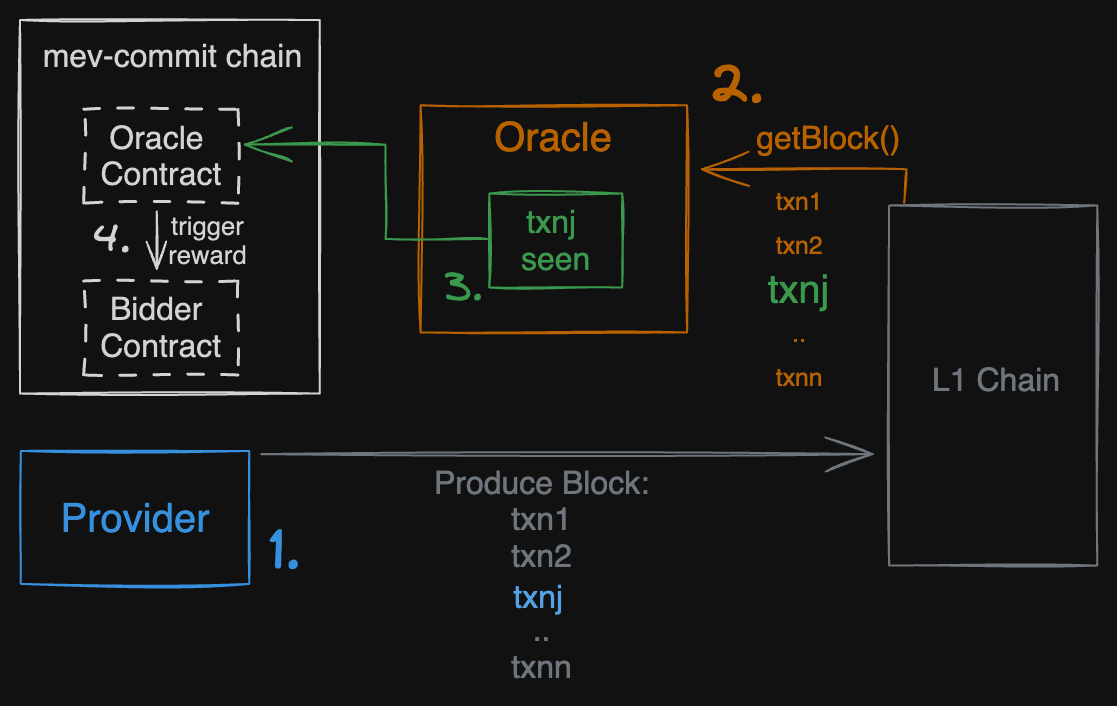
- The provider assembles the complete L1 block, incorporating txnj, to which it previously committed. Note: If the provider doesn’t get selected to construct the L1 block, the oracle flow does not get triggered.
- The oracle microservice fetches the block from the L1 chain and verifies the presence of txnj.
- Upon confirmation that txnj is included, the microservice notifies the oracle smart contract of the commitment’s fulfillment.
- The oracle smart contract then initiates the transfer of funds from the bidder’s deposited balance to the provider’s account.
Oracle Slashing Path
In the event that a provider fails to include a committed transaction (txnj) in the L1 block, the oracle slashing path is initiated to penalize the provider for the breach of commitment. This process is outlined below: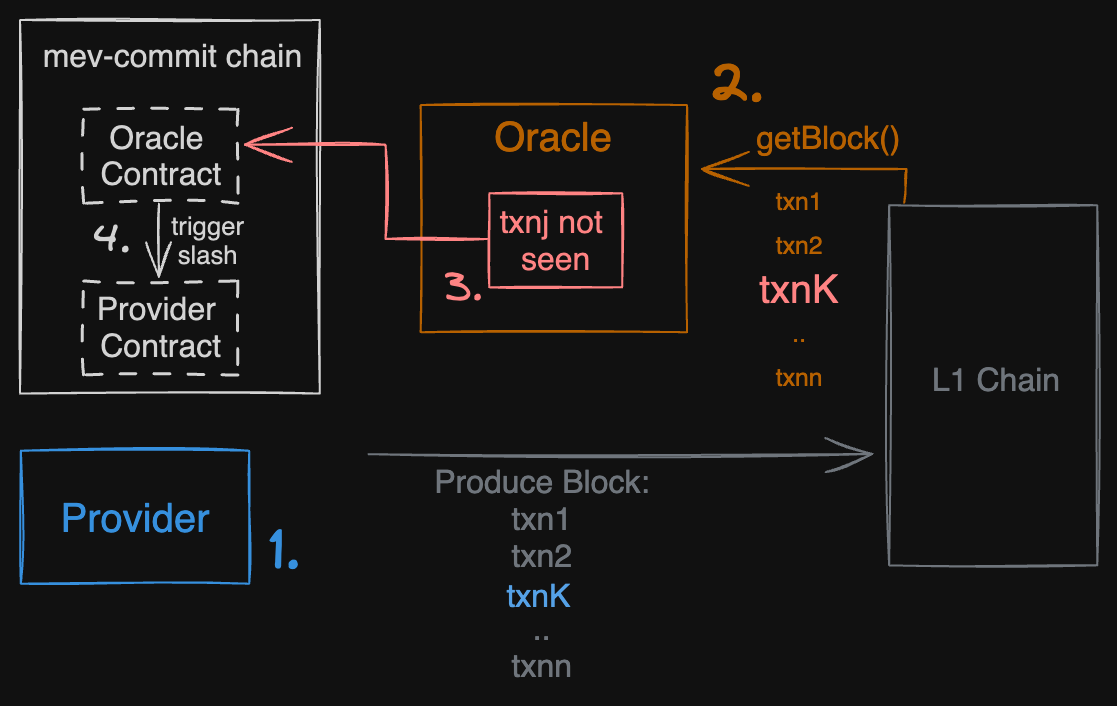
- The provider is expected to produce an L1 block that includes the committed transaction (txnj). However, if the provider does not include txnj, the protocol moves to the slashing phase.
- The oracle microservice retrieves the block from the L1 chain and searches for txnj. If the transaction is not found, it triggers the next step.
- The oracle communicates that txnj was not seen in the oracle contract.
- The oracle contract, upon receiving this information, initiates the slashing procedure. This involves penalizing the provider by triggering a slash event, which results in the forfeiture of the stake held by the provider contract as a guarantee of honest behavior.
- The confiscated stake is subsequently allocated to the bidder as compensation for the provider’s failure to include the committed transaction, thereby ensuring that the bidder is recompensed for the provider’s breach of trust.

